
The highest priority for hospitals is to provide exceptional patient care without interruptions, no matter what happens. Therefore, it is crucial to stay protected against cyberthreats such as viruses or ransomware that may impair operations, compromise patient data, create financial damage, and harm your overall reputation.
We at Siemens Healthineers take a holistic approach to cybersecurity.
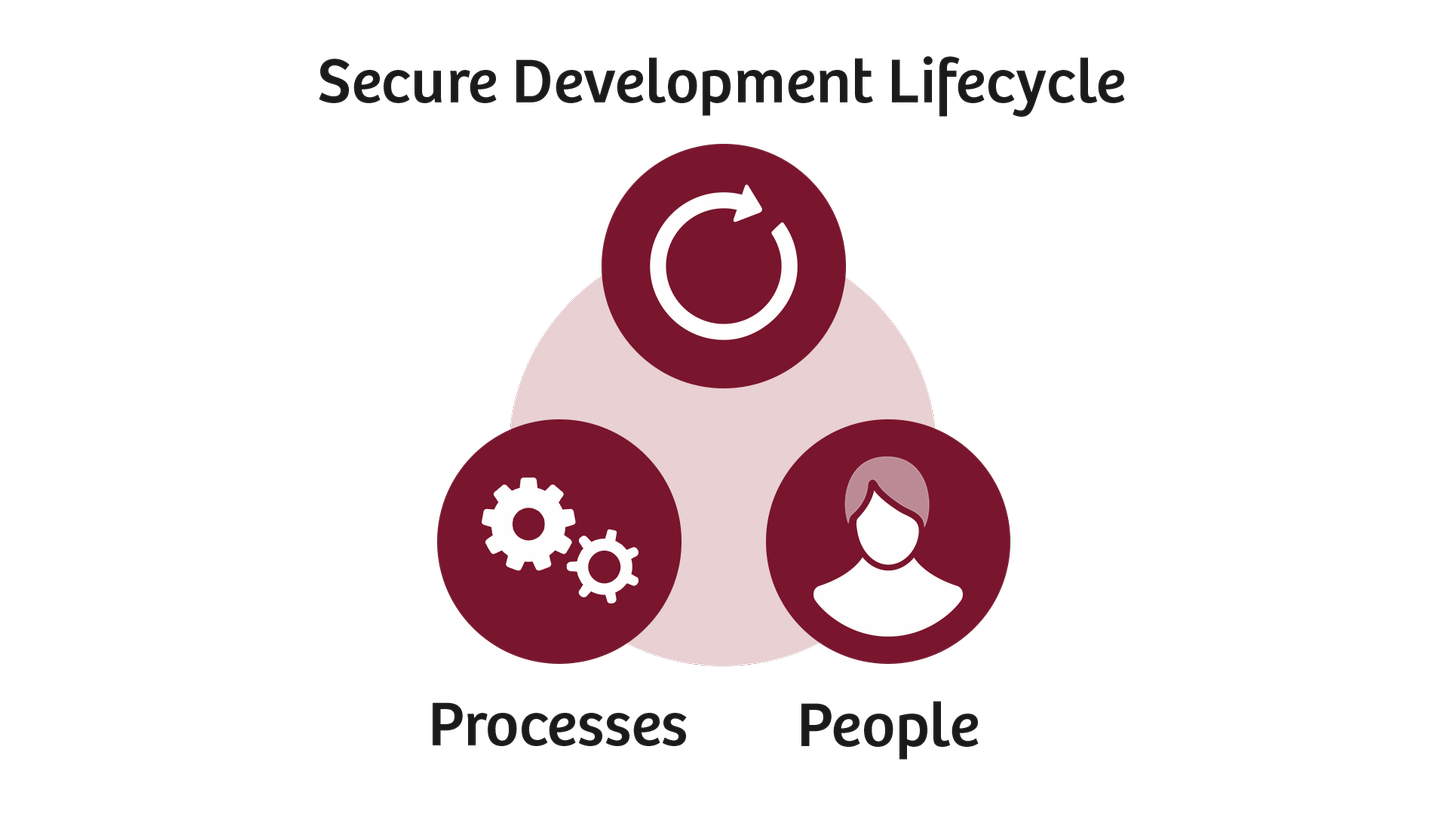
Secure Development Lifecycle: Guided by set security requirements and product-specific threat and risk analyses, we develop our equipment according to internationally accepted standards and procedures. The equipment design aims to minimize attack surfaces and achieve optimal hardening of the technology stack. We continue the hardening process during deployment by applying the latest software updates. In addition to continuous validation and verification, the security posture of our products is evaluated on an ongoing basis using vulnerability scans, fuzz testing, and penetration testing.
People: Protecting medical equipment against cyberthreats is challenging and requires a company culture that values secure operations and privacy protection. We provide regular cybersecurity awareness and role-specific training for management, R&D, logistics, and service personnel.
Processes: Our company-wide processes at Siemens Healthineers provide strict guidelines for mitigating risks posed by identified threats at any point, from equipment development to service provision. These guidelines are constantly adapted and updated.

A shared culture of cybersecurity risk management
Our vigilance when it comes to cybersecurity enables us to deliver equipment that supports your efforts to shield your healthcare institution from threats, protecting your patient data and increasing cost efficiency. All equipment currently under development as well as a range of existing offerings have built-in security controls that can be adapted to your network requirements during deployment. This allows for smooth and protected operations throughout the equipment lifecycle at your site. With our continuous security update process, incident support, and the maintenance services that are available for some products, we cover the vendor part of the responsibility we share when it comes to protecting the operations and data privacy of and inside your institution.

Deployment: protected right from the start
Our equipment ships with a range of security controls, which will be individually configured during deployment depending on the network and security requirements of your medical facility. This supports cybersecurity risk management throughout the equipment lifecycle at your institution.

Operations: custom security controls
Role-based user management allows you to customize access privileges for each user. Along with data encryption and audit trails for change control, this reduces the risk of unauthorized access, data loss or theft, and provides forensic information.

Maintenance: intelligent threat response
We keep track of newly discovered vulnerabilities, so we are able to respond to emerging threats with security updates. Incident support by our experts provides you with hands-on support in the event of a security breach, so your team can reduce further damage and help restore secure system operation.

